Page 168 - {PDF Title}
P. 168
Mhaske and Kumar
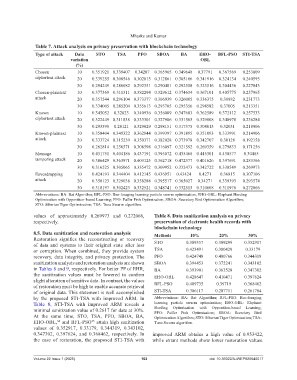
Table 7. Attack analysis on privacy preservation with blockchain technology
Type of attack Data STO TSA PFO SBOA BA EHO- BFL-PSO STI-TSA
variation OBL
(%)
Chosen 10 0.351921 0.339407 0.34287 0.365965 0.349648 0.37791 0.367569 0.253009
ciphertext attack 20 0.339255 0.308546 0.302815 0.312861 0.305106 0.341916 0.324134 0.240593
30 0.294249 0.286082 0.292351 0.290481 0.292558 0.323516 0.304436 0.227043
Chosen-plaintext 10 0.377369 0.311311 0.382294 0.329612 0.374634 0.367101 0.405775 0.257965
attack 20 0.357544 0.296104 0.373377 0.306939 0.326005 0.336375 0.38882 0.231773
30 0.334005 0.285204 0.355613 0.293705 0.295356 0.298582 0.37005 0.213351
Known 10 0.345052 0.32823 0.340936 0.356009 0.347683 0.362589 0.372112 0.257533
ciphertext attack 20 0.322449 0.311838 0.333301 0.327906 0.331565 0.329808 0.340978 0.236284
30 0.293598 0.28121 0.329029 0.298151 0.317375 0.304013 0.32031 0.218906
Known-plaintext 10 0.358404 0.349322 0.362844 0.399397 0.391895 0.351093 0.333991 0.214906
attack 20 0.333724 0.315239 0.350371 0.382028 0.373978 0.342707 0.30128 0.192158
30 0.262814 0.256571 0.308598 0.316097 0.321592 0.269359 0.279833 0.171256
Message 10 0.431751 0.404186 0.437191 0.395072 0.435468 0.445301 0.430577 0.30485
tampering attack 20 0.386429 0.363971 0.403125 0.362718 0.472377 0.401626 0.397691 0.283366
30 0.316525 0.305065 0.335472 0.309952 0.332473 0.342722 0.330549 0.269973
Eavesdropping 10 0.424193 0.344404 0.412145 0.436951 0.43424 0.4271 0.36815 0.307106
attack 20 0.358123 0.329038 0.358288 0.395517 0.365027 0.34271 0.339393 0.293574
30 0.318197 0.302423 0.332521 0.348741 0.332513 0.310608 0.311976 0.272066
Abbreviations: BA: Bat Algorithm; BFL-PSO: Bee-foraging learning particle swarm optimization; EHO-OBL: Elephant Herding
Optimization with Opposition-based Learning; PFO: Puffer Fish Optimization; SBOA: Secretary Bird Optimization Algorithm;
STO: Siberian Tiger Optimization; TSA: Tuna Swarm algorithm.
values of approximately 0.269973 and 0.272066, Table 8. Data sanitization analysis on privacy
respectively. preservation of electronic health records with
blockchain technology
8.5. Data sanitization and restoration analysis Methods 10% 20% 30%
Restoration signifies the reconstructing or recovery
of data and systems to their original state after loss STO 0.389357 0.389299 0.352917
or corruption. When combined, they provide system TSA 0.423491 0.380429 0.33179
recovery, data integrity, and privacy protection. The PFO 0.424748 0.400766 0.344319
sanitization analysis and restoration analysis are shown SBOA 0.394453 0.372241 0.343102
in Tables 8 and 9, respectively. For better PP of EHR, BA 0.393901 0.363528 0.347302
the sanitization values must be lowered to confirm EHO-OBL 0.428647 0.410471 0.397624
slight alteration of sensitive data. In contrast, the values
of restoration must be high to enable accurate retrieval BFL-PSO 0.409735 0.39719 0.368462
of original data. This statement is well accomplished STI-TSA 0.306117 0.287711 0.261784
by the proposed STI-TSA with improved ARM. In Abbreviations: BA: Bat Algorithm; BFL-PSO: Bee-foraging
Table 8, STI-TSA with improved ARM reveals a learning particle swarm optimization; EHO-OBL: Elephant
minimal sanitization value of 0.2617 for data at 30%. Herding Optimization with Opposition-based Learning;
PFO: Puffer Fish Optimization; SBOA: Secretary Bird
At the same time, STO, TSA, PFO, SBOA, BA, Optimization Algorithm; STO: Siberian Tiger Optimization; TSA:
EHO-OBL, and BFL-PSO attain high sanitization Tuna Swarm algorithm.
35
34
values of 0.352917, 0.33179, 0.344319, 0.343102,
0.347302, 0.397624, and 0.368462, respectively. In improved ARM obtains a high value of 0.953422,
the case of restoration, the proposed STI-TSA with while extant methods show lower restoration values.
Volume 22 Issue 1 (2025) 162 doi: 10.36922/AJWEP025040017