Page 161 - {PDF Title}
P. 161
Blockchain for secure e-health data in smart cities
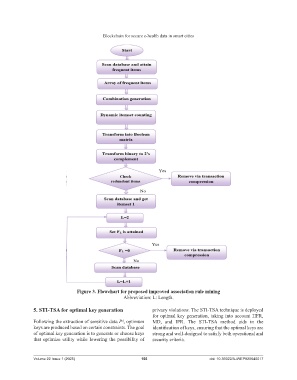
Figure 3. Flowchart for proposed improved association rule mining
Abbreviation: L: Length.
5. STI-TSA for optimal key generation privacy violations. The STI-TSA technique is deployed
for optimal key generation, taking into account HFR,
Following the extraction of sensitive data P , optimum MD, and IPR. The STI-TSA method aids in the
d
keys are produced based on certain constraints. The goal identification of keys, ensuring that the optimal keys are
of optimal key generation is to generate or choose keys strong and well-designed to satisfy both operational and
that optimize utility while lowering the possibility of security criteria.
Volume 22 Issue 1 (2025) 155 doi: 10.36922/AJWEP025040017